views

Image by harshahars on Pixabay
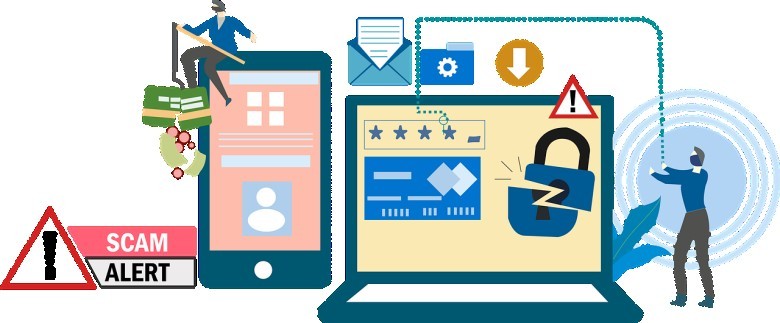
Cyber threats are becoming more pressing as the world moves into the digital age. In 2022, we saw this firsthand when nearly a billion Chinese citizens had their data stolen and sold on the darknet. This event is a sobering reminder of how serious cyber threats can be and why staying up-to-date with cybersecurity best practices is essential.
As we go further into 2023, here are some critical tips for protecting yourself online and staying safe from malicious actors.
Why Cybersecurity Is Important in 2023
Cybersecurity will be more critical than ever in 2023. Cyber threats and attacks become a greater risk as people increasingly rely on digital technologies. Cybercriminals are more sophisticated, using advanced techniques such as exploiting zero-day vulnerabilities or deploying ransomware campaigns.
Furthermore, the pandemic has made it easier for malicious actors to take advantage of people, as digital tools have become an integral part of our everyday lives. As a result, it is crucial to ensure you are taking every step necessary to protect yourself online.
Cybersecurity Threats to Watch Out For in 2023
Here are some of the most prevalent cybersecurity issues and threats to be careful of in 2023:
Ransomware
Ransomware is malicious software restricting access to the victim’s data until a ransom is paid. It is one of the most dangerous cyber threats in 2023, as it can disable computers and networks, preventing users from accessing important information. Cybercriminals will typically demand cryptocurrency payment to decrypt the blocked data.
Ransomware attacks are becoming increasingly sophisticated as attackers use more advanced techniques, targeting specific individuals or organizations.
Phishing
Phishing is one of the most common forms of cyber attacks in 2023. It involves attackers sending out messages or emails that look like they are from a legitimate source. These messages typically contain malicious links or attachments that can infect a computer with malware once clicked on.
Unfortunately, these phishing attacks are becoming increasingly sophisticated, using tactics such as social engineering or even cloning corporate websites to fool victims into handing over personal information.
Malware
Malware is another common threat to look out for. It is malicious software that is designed to infiltrate a system and cause damage. Cybercriminals use malware to steal information, take control of computers and networks, and even demand payments from victims. Hackers can deliver malware through various vectors such as email, websites, downloads, or malicious links.
In 2023, malware threats are becoming increasingly sophisticated. Malware is designed to evade traditional security solutions and attack specific targets, making it difficult for companies to protect their networks from cyber threats. Furthermore, attackers are using malware for more than just data theft; they have also started deploying ransomware campaigns, which can be even more disruptive.
Insider Threats
Insider threats are an increasingly common cybersecurity risk in 2023, as attackers exploit the trust of insiders to access sensitive information or disrupt operations. Insider threat actors can be disgruntled employees, contractors, or careless individuals who unknowingly put their organization at risk by neglecting security protocols.
Malicious insiders target organizations for financial gain, corporate espionage, or sabotage. Careless insiders are often unaware of the risks associated with their actions. They can be a source of unintentional data leakage. That could include using unsecured devices for work activities, revealing confidential information on social media platforms, or failing to adhere to security protocols.
Image by Fidsor on Pixabay
Best Practices To Combat Cybersecurity Threats
Here are some of the best practices to combat these cybersecurity issues and threats:
Using strong passwords
Coming up with a strong password is one of the essential steps to protect yourself from cyber threats. Strong passwords are long, complex combinations of letters, numbers, and symbols that are difficult for hackers to guess. When creating a password, ensure it’s at least eight characters long and includes a mix of upper and lower case letters, special characters, and numbers.
Additionally, avoid using identifiablewords or phrases, such as your name, birthdate, or common terms. It’s also essential to not use the same password for multiple accounts; instead, create unique passwords for each account. If you find it difficult to remember all your passwords, consider using a password manager that stores and manages them securely.
Lastly, change your passwords regularly and never share them with anyone. By following these simple best practices, you can significantly reduce the risk of having your accounts compromised by cybercriminals.
Implementing two-factor authentication
Two-factor authentication, also known as 2FA, is an added layer of security used to protect online accounts. Before allowing access, this process requires two pieces of evidence, such as using biometric authentication like fingerprints or face recognition. They can also use secure tokens and one-time passwords (OTPs). Two-factor authentication helps prevent cybercriminals from accessing an account even if they obtain login credentials.
2FA can be implemented in various ways, such as using biometric authentication like fingerprints or face recognition or using secure tokens and one-time passwords (OTPs). Many companies now employ 2FA to protect their employees’ accounts. At the same time, other services offer 2FA as an option to protect customers’ accounts better.
Additionally, you can use two-factor authentication with other security measures, such as multi-factor authentication and single sign-on, which provide extra layers of protection against cyber attacks. By implementing 2FA, organizations can significantly reduce their risk of data breaches due to malicious actors or irresponsible insiders.
Keeping software updated
Keeping software up-to-date is essential for staying protected from the ever-evolving cybersecurity threats of 2023.
You need to implement security patches and address any vulnerabilities or bugs in the system, as hackers are vigorously looking for ways to exploit these flaws. Organizations must ensure their systems are regularly patched and updated to protect against malware and other attacks.
It’s also essential to ensure that all software applications operate at the latest versions to benefit from the most recent security features. Furthermore, organizations should consider implementing an automated patch management system or using a third-party vendor to manage patches and updates.
By taking these proactive steps, organizations can reduce the risk of their systems being compromised due to unpatched vulnerabilities.
Using a VPN
A Virtual Private Network (VPN) is a secure connection to the internet that masks your online activity. When you route your traffic to a VPN, all your data is redirected through an encrypted tunnel and routed to a remote server so that no one can track or monitor your online activity.
Using a VPN has several benefits, such as providing anonymity, browsing the web safely, protecting your data from hackers and government surveillance, and allowing you to access geo-restricted content. Additionally, VPNs have servers located worldwide, making overcoming censorship or internet restrictions easier.
With the right VPN provider, organizations can also benefit from a secure remote connection that enables their employees to access the company network securely anywhere in the world. Moreover, you can use VPN technology to protect corporate data when accessed over public Wi-Fi networks.
Organizations and individuals can benefit from increased security and privacy while browsing online using a VPN. It’s important to note that you should only use a high-caliber VPN provider to ensure your data and online activity remain private and secure.
Backing up your data
Backing up your data is essential in protecting against cyberattacks, data loss, and other digital threats. Having a secure backup plan allows organizations to quickly recover their data if it is lost due to malicious or accidental causes. Regularly backing up data can also reduce costs associated with system downtime and restore operations quickly without the need for costly recovery processes.
When creating a backup plan, organizations should consider the type of data they need backing up and how often it is needed. It’s also essential to have multiple copies of the backups in case one fails or is compromised. All backups should be encrypted with strong passwords and stored in secure off-site locations.
By backing up data regularly, organizations can ensure their critical data remains safe and secure even during a security breach or system failure. With a good backup strategy, organizations can be confident that they have a reliable way of recovering their data quickly and efficiently.
Using antivirus software
Antivirus software is essential to cybersecurity and protects systems from malicious software, viruses, and ransomware. Antivirus programs are designed to detect, block, and remove malicious code that can compromise computers and networks. That includes malware such as worms, Trojans, spyware, adware, rootkits, and ransomware.
By running regular scans, antivirus software can identify and remove any malicious threats before they have a chance to cause damage. Additionally, you should train your employees to recognize signs of virus infections and respond appropriately if a threat is detected.
Organizations should use an up-to-date antivirus program with the latest definitions to ensure optimal protection from the latest threats. Additionally, you should train your employees on recognizing signs of virus infections and responding appropriately if a threat is detected.
Image by TheDigitalArtist on Pixabay
Enabling firewalls
Enabling firewalls is essential in protecting against digital threats and online data breaches. Firewalls are specifically designed to block unauthorized access to a network or server by creating a barrier between trusted and untrusted sources. You can customize firewall configurations to allow only certain connections and traffic while blocking malicious attempts to access the system.
In addition to blocking malicious traffic, you can also use firewalls to monitor and log activity on a network. That allows organizations to detect suspicious activity or attempts at unauthorized access in real time. Firewalls can also be configured to block specific types of websites or applications which may pose a security risk.
Monitoring your network
Monitoring your network is essential in maintaining security and preventing data breaches. It allows organizations to detect suspicious activity or attempts to access the system in real-time, allowing for quick response and mitigation of potential threats. Network monitoring also helps organizations identify potential vulnerabilities in their systems, addressing them before hackers can exploit them.
You can use network monitoring to track user activity, detect any malicious code or suspicious connections, and even identify weak passwords. By monitoring the network regularly, organizations can quickly identify potential threats before they become significant issues. Additionally, regular monitoring allows organizations to create detailed reports of their network activity which can be used for future reference.
The Bottom Line
In summary, organizations can take various measures to protect their networks from digital threats and online data breaches. These include backing up data regularly, using antivirus software with the latest iterations, enabling firewalls for added protection, and monitoring your network continuously.
By following these steps as part of a comprehensive cybersecurity strategy, organizations can keep their systems secure while ensuring that critical information remains safe. With the right security plan, companies can have peace of mind knowing they’re doing everything possible to protect themselves against cyber attacks.
Related: A Guide to Staying Safe on Neighborhood Apps (2023)






















Comments
0 comment